Get 20% off this month when you try our services!
Services we offer
Nothing is too big or too small for us the services that we offer can come from desktop repair to network repair.
- Vulnerability scans
- Penetration testing
- Desktop Service
- Voip Phones
- Server Virtualization
- Email Hosting
- Data Recovery
- Data backups
- Ransomware
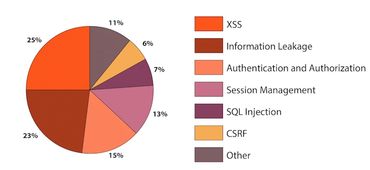
VULNERABILITY SCAN
Vulnerability scanning is vital for every company to make sure you are protected and up to date with the latest security update. With a vulnerability scan your network will be scanned to check for known vulnerabilities that may need attention. With SecureITNowSolutions we use software and tools to make sure you your system is as patched and secure.

penetration testing
Penetration testing is very similar to the Vulnerability scanning but with a few differences. One of the main difference is that its a authorized attack on a computer system or network designed to evaluate the security of the system and its key weaknesses. These attacks are ways to gain access to a system’s features or data. With Penetration testing we compiles a risk assessment of the entire system to aid in determining whether a system is vulnerable to an attack.
There are typically five stages of penetration testing:
- Reconnaissance – Gathering information on the system to be targeted.
- Scanning – used to further the attacker’s knowledge of the system.
- Gaining Access – Using previously collected data, the attacker can target an exploit in the system.
- Maintaining Access – Taking steps to remain within the target environment to collect as much data as possible.
- Covering Tracks – The attacker must wipe all trace of the attack from the system including any type of data collected, or events logged, to remain anonymous.